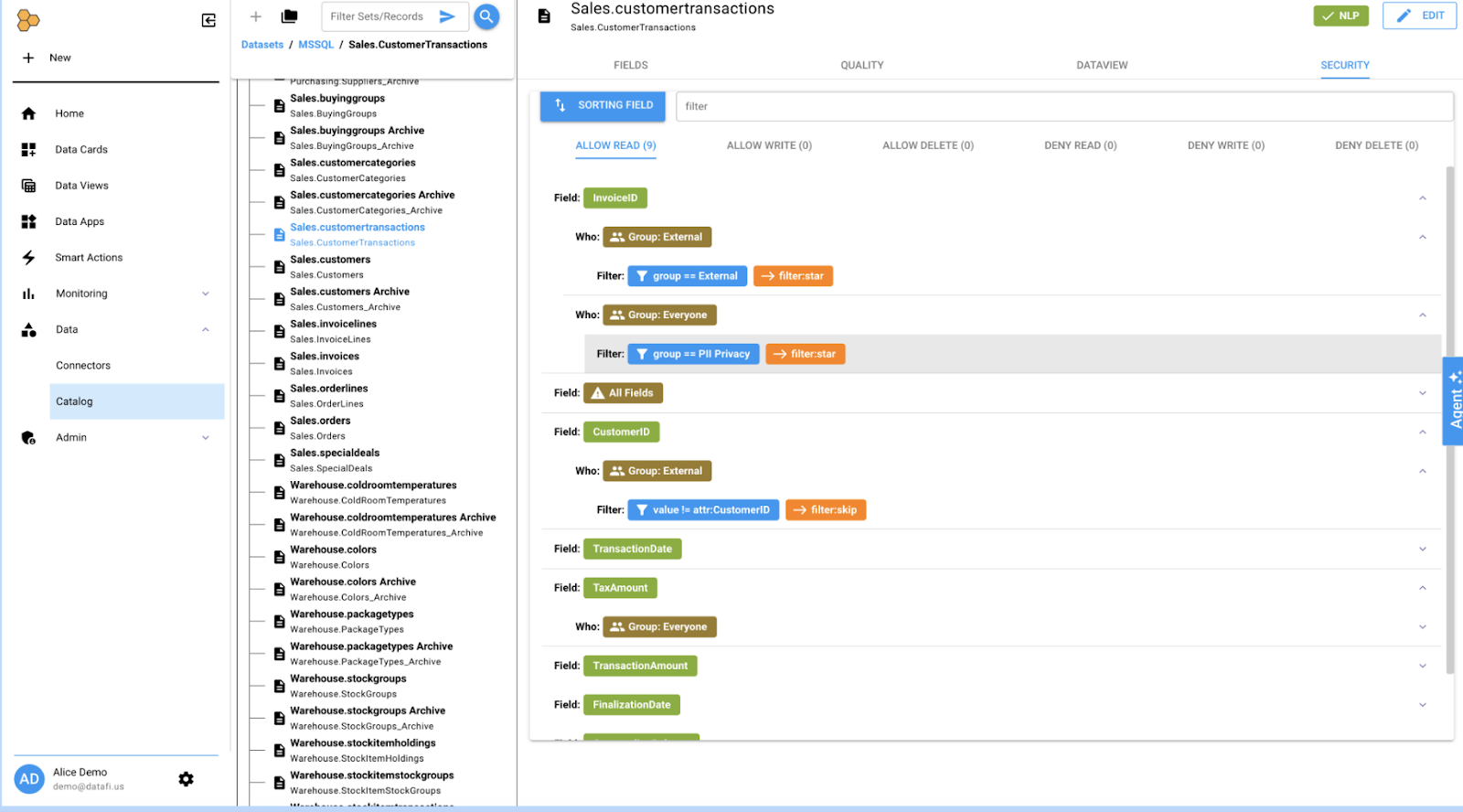
Datafi prioritizes security through Attribute-Based Access Control (ABAC), a modern authorization approach that surpasses traditional access management methods.
ABAC evaluates multiple attributes dynamically at decision time — including user identity, resource classification, action type, and contextual factors — rather than relying on fixed roles or static permission lists. This makes access decisions more precise, adaptive, and aligned with real-world security needs.
Understanding ABAC vs. Traditional Access Control
ABAC grants access based on attributes connected to users, data, actions, and context rather than fixed roles or lists. Unlike older models — Mandatory Access Control (MAC), Discretionary Access Control (DAC), and Role-Based Access Control (RBAC) — ABAC evaluates multiple attributes dynamically at decision time.
Typical attributes include:
- User: Department, clearance level, job role
- Resource: Classification, owner, content type
- Action: Read, write, delete
- Context: Time of day, location, device
Why ABAC Is a Game-Changer
Access Control and Identity Management in Datafi
Datafi implements granular ABAC policies ensuring users access only authorized data. Unauthorized queries return no results, preventing accidental exposure. The platform integrates with enterprise identity providers including Okta, Azure AD, and Active Directory, supporting single sign-on (SSO) and federated authentication. Organizations can enforce corporate login policies, including multi-factor authentication, and manage centralized provisioning or deactivation. Datafi maintains audit logs tracking access activities to support governance and forensic analysis.
Industry Examples of ABAC in Action
AWS
Cloud computing platforms embrace ABAC at scale. AWS Identity and Access Management uses tags as attributes to grant dynamic permissions. A developer can start or stop any cloud server if the server’s “project” tag matches the developer’s project attribute, demonstrating flexibility in large environments.
Data Governance Platforms (Immuta, Okera)
These solutions restrict data at row, column, or cell levels based on attributes like user clearance or usage purpose. Immuta’s dynamic ABAC approach proves more nuanced than older Apache Ranger’s static role-based system, particularly valuable for enforcing privacy regulations like GDPR and HIPAA through regulatory attributes.
Data Catalog Tools (Collibra, Alation)
Enterprise data catalogs increasingly support attribute-based controls. Collibra integrates with policy engines like SecuPi for enforcement, while Alation partners with Immuta or Privacera. Attribute-based rules determine whether catalog users can preview or query datasets.
Enterprise and Government Use
U.S. military branches and the Department of Commerce mandate ABAC practices. Google’s BeyondCorp security model treats user and device attributes as the access foundation — a zero-trust application. Financial institutions employ ABAC to enforce least-privilege principles, ensuring traders and analysts access only authorized client or account data rather than maintaining thousands of custom roles.
Conclusion
ABAC represents a proven security model used by leading organizations, distinguishing Datafi from legacy platforms relying on roles or manual permissions. Through ABAC, Datafi aligns with industry best practices in cloud infrastructure and advanced data governance.
The bottom line
By embracing ABAC, Datafi aligns with industry best practices established by leading cloud providers, government agencies, and data governance platforms. ABAC delivers the dynamic, fine-grained security that modern organizations need — ensuring the right people access the right data under the right conditions, every time.